Browse Resources
Information and Security Technologies -- Security, information assurance, and forensics
Resources |
|---|
This PDF document, provided by the Ohio Region Cybersecurity Technician Training Pipeline at Columbus State Community College, outlines a job description for an entry-level cybersecurity technician. The document lists the various roles that these professionals play and provides the corresponding...
In this podcast episode, published by the Center for Occupational Research and Development, John Sands from Moraine Valley Community College discusses the importance cybersecurity education for technicians in different disciplines. Sands highlights how the interconnectedness of modern systems leads...
This 42-page report, from the National Cyberwatch Center, includes information on cybersecurity apprenticeships. This resource is primarily intended for federal cybersecurity human resources and hiring managers. During over a year long effort "... a working group of 15 federal, academic, and...
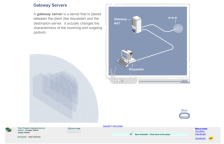
This brief interactive activity, by Electromechanical Digital Library and Wisconsin Technical College System faculty members Joseph Wetzel and Brian Gremore, provides a lesson on gateway servers to further illustrate how data travels on the Internet. The illustrations and animations help...
This brief interactive activity, by Electromechanical Digital Library and Wisconsin Technical College System faculty members Joseph Wetzel and Douglas Tabbutt, provides a basic lesson on firewalls. This learning activity introduces the purpose of a firewall and a simple overview of what a firewall...
This brief interactive activity, by Electromechanical Digital Library and Wisconsin Technical College System faculty members Joseph Wetzel and Douglas Tabbutt, provides an interactive lesson on packet filters to demonstrate their use. After a brief explanation, there is an activity that allows the...
This brief interactive activity, by Electromechanical Digital Library and Wisconsin Technical College System faculty members Joseph Wetzel and Brian Gremore, provides a basic introduction to stateful packet inspectors (SPIs). This online lesson gives a definition, examples, and explanation of SPIs...
This paper, published in Advances in Digital Forensics VII, discusses the unique challenges that plug computers pose to evidence recovery operations during criminal investigations. Plug computers are a cross between an embedded device (such as a smart phone) and a traditional computer. The...
Program Description:
River Valley Community College, in association with Program Development in Cybersecurity with Focus on Business and Healthcare Concepts, has developed a 4-semester program to prepare students to working the Information Assurance (IA) field with a focus on Cybersecurity and...
This webpage, from National Cybersecurity Training and Education (NCYTE) Center, includes governance, risk management, and compliance workshops that were "designed for college faculty that teach cybersecurity and information assurance programs who recognize that community college cybersecurity...
|
| ← PreviousNext → |